Cisa Software Supply Chain
The Cybersecurity and Infrastructure Security Agency (CISA) has become increasingly focused on the software supply chain as it is an integral part of national security. The software supply chain encompasses all the processes involved in the development, deployment, and management of software products—from the creation of code to its use in final products. This chain may involve multiple entities, including software developers, vendors, integrators, and end-users, each of which can introduce vulnerabilities or be targeted by cyber-attacks.
One of the key initiatives led by CISA is to ensure the integrity and security of the software supply chain through a series of guidelines, best practices, and security frameworks. These initiatives include collaboration with public and private entities to establish comprehensive security measures throughout the software lifecycle. The agency has worked on various fronts, such as enhancing the transparency of software components, promoting standardized software bill of materials (SBOM), and fostering real-time information sharing regarding threats and vulnerabilities.
Software Bill of Materials (SBOM) is particularly critical in CISA's strategy to secure the software supply chain. An SBOM provides detailed information about the components contained in a software product, similar to a list of ingredients in packaged food. This transparency allows organizations to understand the origins of the software they are using, manage licenses, and respond promptly to vulnerabilities.
CISA also emphasizes the use of automated tools and continuous monitoring systems to detect and mitigate risks within the software supply chain. Continuous integration and continuous deployment (CI/CD) practices are recommended to ensure that security checks are embedded into every stage of the software development process. Moreover, CISA promotes the adoption of strong identity access management practices and authentication mechanisms to prevent unauthorized access to software resources.
Overall, CISA’s comprehensive approach to securing the software supply chain encompasses a mix of policy-making, stakeholder collaboration, and technical measures designed to fortify the entire ecosystem against potential threats. The objective is to not only protect critical infrastructure but also to enhance the overall resilience of software ecosystems in the face of evolving cyber threats.
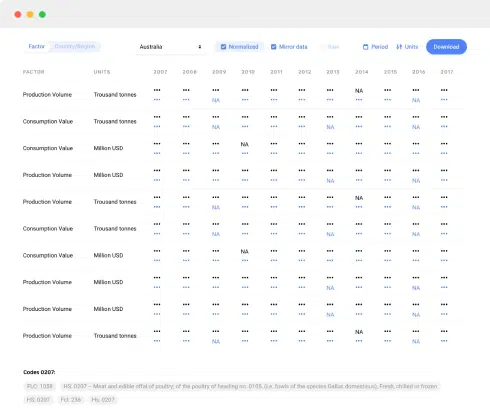
Nothing found. Please try again.
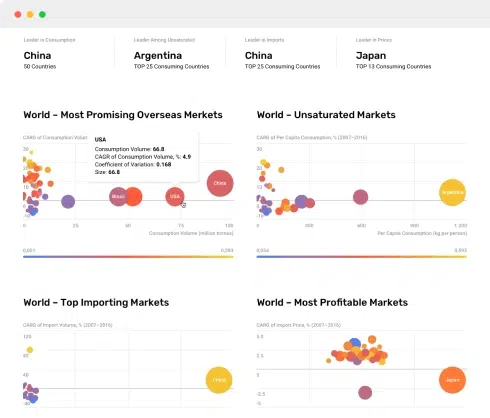
Nothing found. Please try again.
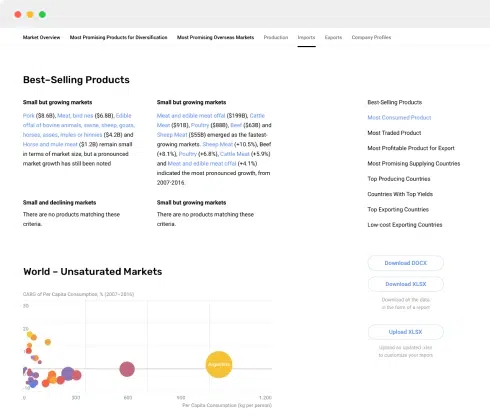
Nothing found. Please try again.